Hello, Engineers! This is Hermes Solution. Have you heard about Tesla’s Cybertruck?
Tesla’s unique pickup truck model, the Cybertruck, has captivated the global automotive market with its futuristic design and innovative electric vehicle performance. As we move into the era of connected cars, vehicles have evolved beyond simple modes of transportation into highly integrated devices. Naturally, this shift has brought cybersecurity issues to the forefront. In this post, we will explore the key cybersecurity challenges the Tesla Cybertruck might face and Tesla’s strategies to address them.

1. Wireless Key (Fob) and Mobile App Attacks
One of the most commonly mentioned cybersecurity issues is smart key hacking. Tesla vehicles use wireless keys or mobile apps to unlock doors and start the car. However, relay attacks that amplify these signals have led to car theft incidents. For instance, multiple cases of electric car theft, including Tesla vehicles, have been reported in regions like the UK.
Additionally, hacking into the Tesla mobile app account could allow remote vehicle control and even location tracking, posing a significant threat to car owners.
Countermeasures:
PIN to Drive: Require a PIN before starting the car.
Key Fob Sleep Mode: Automatically disable signal transmission when the key is out of range.
Two-Factor Authentication (2FA): Enhance security for the mobile app account.
2. Hacking the In-Vehicle Network (CAN Bus)
Electronic control units (ECUs) inside vehicles communicate via networks like the CAN bus. Past hacking competitions (e.g., Pwn2Own) and security research have revealed vulnerabilities in Tesla Model S that allowed control over acceleration and braking. Such cybersecurity risks could also emerge in the Cybertruck’s complex internal network.
Countermeasures:
Reinforced Gateways: Block unauthorized packets between ECUs.
Intrusion Detection Systems (IDS): Detect abnormal signals in real-time.
Code Signing & Integrity Checks: Regularly verify ECU firmware for tampering.
3. OTA (Over-The-Air) Update Manipulation
Tesla vehicles, including the Cybertruck, manage software remotely via OTA updates. While this technology significantly improves user convenience, it also introduces the risk of malicious software being inserted during data transmission, exposing the entire vehicle to serious cybersecurity threats.
Countermeasures:
Code Signing & Encryption: Encrypt data for OTA updates.
End-to-End Encryption: Ensure secure communication between servers and vehicles.
Regular Security Patches: Quickly respond to newly discovered vulnerabilities.
4. Disruption of Autonomous Driving Sensors and AI
The Cybertruck incorporates Tesla’s autonomous driving technology (e.g., Autopilot, Full Self-Driving). However, techniques like GPS spoofing and adversarial attacks could disrupt sensors and AI systems. For example, cleverly manipulated road signs might cause AI to make incorrect decisions.
Countermeasures:
Sensor Fusion: Combine data from cameras, radar, IMUs (Inertial Measurement Units), and more to enhance accuracy.
Regular AI Model Updates: Continuously refine AI models to address vulnerabilities and incorporate new data.
5. Tesla’s Cybersecurity Strategy
Tesla is a leading automotive manufacturer when it comes to addressing cybersecurity. Here are some of its key initiatives:
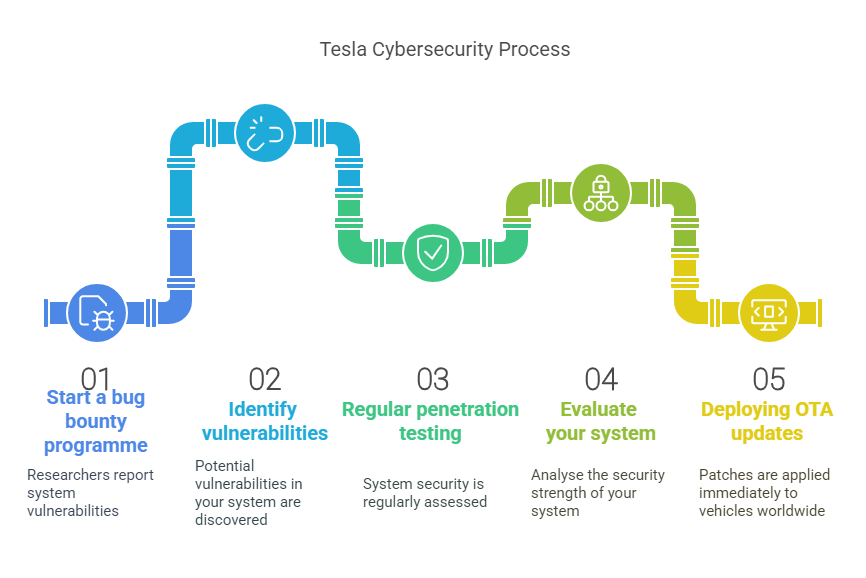
Bug Bounty Program: Reward security researchers for identifying vulnerabilities in Tesla’s systems, fostering a proactive approach to security.
Regular Penetration Testing: Conduct thorough security evaluations during development and obtain external verification even after product release.
Rapid OTA Patching: Deploy OTA updates immediately to address vulnerabilities across the fleet. This is considered one of Tesla’s greatest strengths.
“Cybersecurity Continues to Evolve”
The Tesla Cybertruck is likely to face similar cybersecurity challenges as its predecessors. However, Tesla’s proactive measures allow the company to address these threats swiftly. While perfect security may be unattainable, Tesla’s culture of quick patching and transparent responses strengthens its reputation as a trusted brand.
“Security threats don’t disappear. What matters is how quickly you respond to them.”
We look forward to seeing the Tesla Cybertruck establish itself as a powerful and secure electric pickup truck based on this philosophy.
If your company’s vehicles or connected technologies are facing similar cybersecurity challenges, Hermes Solution is here to help. With trusted security consulting and innovative solutions, we can alleviate your concerns. SAFETY FIRST!











