Hello, engineers! This is Hermes Solution. Today, we’ll be discussing cybersecurity vulnerabilities in V2X (Vehicle-to-Everything) communication, a technology gaining attention in the automotive industry, and effective countermeasures against these threats. As real-time communication between vehicles and external environments increases, the importance of V2X security and cybersecurity is growing. In this post, we’ll look at major cybersecurity threats that may arise in V2X communication and explore effective countermeasures.
The Rapidly Growing V2X Market and Cybersecurity Challenges
V2X technology is advancing rapidly in the automotive industry, and multiple research institutions predict high growth rates. For example, by 2028, the market is expected to reach USD 6.84 billion with a CAGR of 44.7%, reaching USD 233.78 billion by 2031. Key trends include the expansion of C-V2X pilot projects, integration with 5G technology, adoption of AI, and the expansion of cloud-based infrastructure. Cloud platforms for real-time data processing and vehicle communication are actively being developed, led by countries like Japan, China, and South Korea in the Asia-Pacific region. As V2X expands, the increase in vehicle connectivity necessitates the application of cybersecurity technologies to ensure secure communication and data protection.
Components of the V2X System
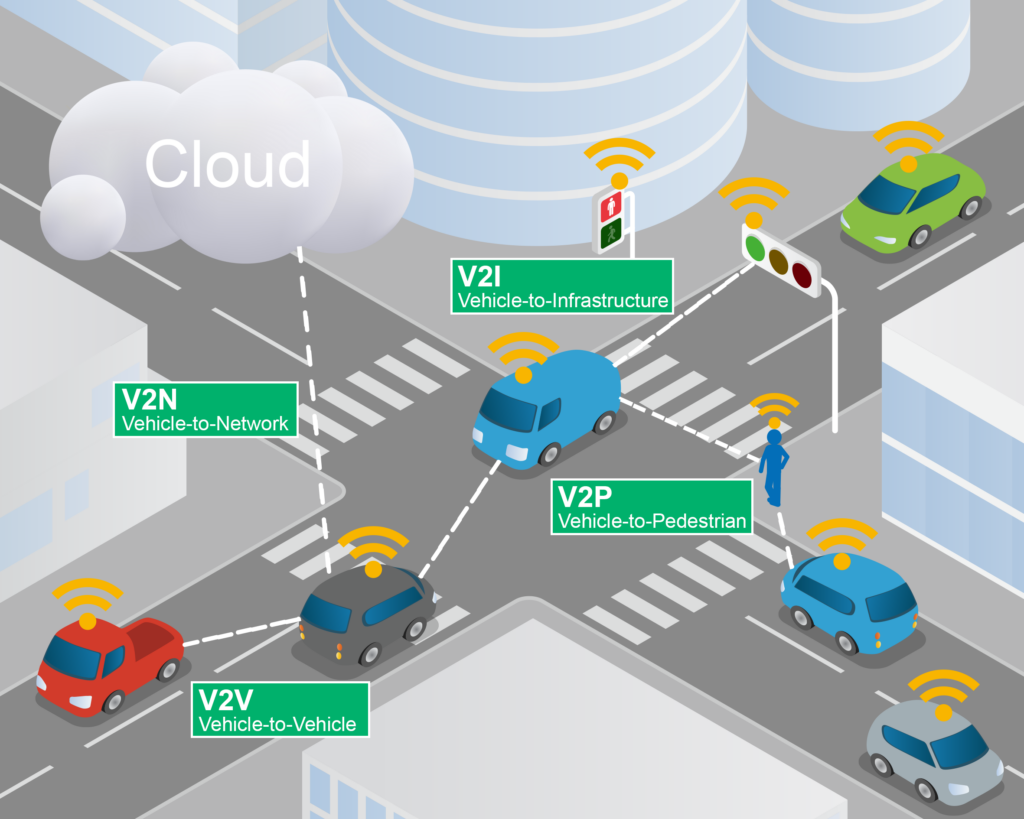
The V2X system comprises On-Board Units (OBUs) installed in vehicles, Road-Side Units (RSUs), traffic information centers, and TCP/IP-based network infrastructure. V2X communication is classified by purpose into Vehicle-to-Vehicle (V2V), Vehicle-to-Infrastructure (V2I), Vehicle-to-Pedestrian (V2P), and Vehicle-to-Network (V2N) communication. Each component has different security requirements, and cybersecurity plays a crucial role across all components.
Cybersecurity Threats in the V2X Communication Environment
Various cybersecurity threats can occur in the V2X communication environment. In a V2V environment, attacks such as message spoofing, false information provision, and attacks through spoofed RSUs/OBUs are possible. In a V2I environment, DDoS attacks, traffic information center hacking, and RSU attacks can manipulate traffic information. These security threats can cause serious issues such as hindering autonomous driving, violating privacy, and causing accidents. Strong authentication systems, encrypted communication, and real-time anomaly detection are urgently needed to secure external communication.
Vulnerabilities in V2X Communication and Cybersecurity Technologies
Security vulnerabilities in V2X communication arise from three aspects: wireless communication security, access control, and application security. Wireless interfaces (Bluetooth, WiFi, GPS) and V2X communication processes are vulnerable to message spoofing and communication disruption. Additionally, unauthorized access to platforms or weak access control poses a significant risk of data leakage. Cybersecurity threats also exist due to third-party application vulnerabilities, which can lead to malware infection or sensitive data exposure.
To address these issues, a multi-layered security approach is required. For wireless communication security, strong encryption protocols and TLS/SSL-based secure communication should be implemented. For cloud protection, PKI-based multi-factor authentication and real-time access monitoring systems should be established. For application security, cybersecurity verification for third-party apps and communication control through API security gateways are essential.
Encrypted Communication for Secure Data Transmission
Encrypted communication is a core element of cybersecurity in the V2X environment, protecting sensitive information such as driving data, location data, and control commands. CAN (Controller Area Network) communication within the vehicle originally emphasized reliability over security, making it vulnerable to data sniffing or manipulation. To address these security vulnerabilities, Secure CAN, which supports message encryption and authentication, and CAN FD (Flexible Data-rate), which offers high bandwidth and security features, have been developed and implemented. For external V2X communication, TLS/SSL protocols are used to ensure end-to-end secure communication. Recently, post-quantum cryptography (PQC) is being actively discussed to address potential vulnerabilities in existing encryption schemes due to the advent of quantum computers.
PKI for Reliable Authentication
PKI serves as the cybersecurity foundation that verifies and authenticates the identity of all entities participating in V2X communication. Through digital certificates issued by certification authorities, PKI enables secure key management and digital signature verification for vehicles, infrastructure, and pedestrian devices. This effectively blocks communication attempts by spoofed vehicles or unauthorized devices. Recently, Decentralized PKI (DPKI) technology, which leverages blockchain technology to reduce dependency on centralized certification authorities, is gaining attention, aiming to establish a safer and more efficient cybersecurity authentication framework.
Security Verification to Block Threat Elements
Security verification is a critical process for ensuring the safety of applications installed in vehicles. It involves source code vulnerability scanning through static analysis, runtime behavior monitoring through dynamic analysis, and penetration testing through simulated hacking. Additionally, verifying compliance with industry standards and evaluating the fulfillment of security requirements ensure security adequacy. This systematic verification process protects vehicle systems from cybersecurity threats such as malware infections or unauthorized function execution.
API Access Control to Prevent Unauthorized Access
API access control is a cybersecurity technology that ensures secure interaction between vehicle systems and external services. It restricts access to authorized services only and effectively blocks external threats through an API gateway. This access control framework prevents cybersecurity incidents caused by unauthorized access or abnormal API calls.
By establishing a secure cybersecurity framework for V2X communication, we can create a safer and more reliable vehicle communication environment. However, since cybersecurity technologies related to V2X continue to evolve, it is essential to monitor the latest trends and establish flexible security strategies to respond to new threats.
Conclusion
The cybersecurity vulnerabilities and countermeasures discussed in this post are essential for ensuring the safety of connectivity and autonomous driving in the V2X era. By building a secure cybersecurity framework in the V2X environment, we can create a more reliable vehicle communication ecosystem. Hermes Solution is dedicated to supporting the establishment of a secure V2X environment through research on the latest cybersecurity technologies. We will continue to be a trusted partner in advancing automotive cybersecurity. Thank you!












